Running a business in Pittsburgh means protecting your assets, employees, and sensitive information around the clock. While traditional locks and keys served businesses for decades, modern commercial security demands smarter solutions. Access control systems have become the cornerstone of comprehensive security strategies, offering Pittsburgh business owners unprecedented control over who enters their facilities and when.
An access control system is an electronic security solution that regulates entry to your business premises, specific rooms, or restricted areas. Unlike traditional key-based systems, these digital solutions combine hardware, software, and security policies to create multiple layers of protection for your commercial property.
When someone attempts to enter a secured area, the system follows a precise four-step verification process. First, it authenticates the person’s identity using their credential: whether that’s a key card, smartphone app, or biometric scan. Next, it checks authorization to determine if they have permission to access that specific area at that particular time. If approved, the system grants access by unlocking the door electronically. Finally, it creates an audit trail by recording who accessed what areas and exactly when, creating detailed security logs essential for investigations and compliance requirements.
This systematic approach eliminates the security gaps inherent in traditional key systems while providing complete visibility into your facility’s access patterns. Every entry attempt: successful or denied: gets logged automatically, creating a comprehensive record that many Pittsburgh businesses find invaluable for both security and operational insights.
Credentials serve as the digital “keys” in modern access control systems. Today’s options include RFID cards or key fobs, mobile credentials through smartphone applications, biometric authentication using fingerprints or facial recognition, and traditional PIN codes entered on keypads. Many Pittsburgh businesses are transitioning to 13.56 MHz smart cards or mobile app credentials because they offer enhanced security through advanced encryption and are difficult to duplicate or compromise.
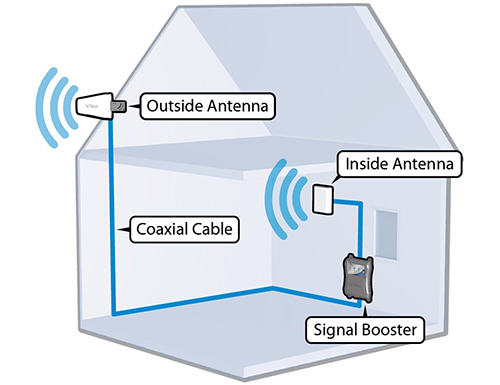
The control panel acts as the system’s brain, managing all credential verification and access decisions. Cloud-based systems handle this processing remotely, reducing the need for on-site hardware while providing greater flexibility for multi-location businesses throughout the Pittsburgh area.
Management software gives you complete administrative control through web or mobile interfaces. Modern platforms offer live monitoring capabilities, remote door control, integrated badge printing, video surveillance integration, and comprehensive reporting features. This software becomes your command center for managing everything from employee credentials to temporary contractor access.
Access points represent the physical locations where entry is controlled: doors, gates, turnstiles, or any restricted area within your facility. These connect to your control system and can be configured with different security levels based on your business needs.
Most Pittsburgh commercial businesses benefit from Role-Based Access Control (RBAC), where permissions are assigned based on job functions or departments rather than individuals. This approach simplifies administration significantly. For example, your accounting team automatically receives access to financial areas, while your IT staff can enter server rooms and technical spaces. When employees change roles or new team members join, you simply assign them to the appropriate role rather than configuring individual permissions.
Discretionary Access Control (DAC) provides business owners with complete control over individual access decisions. While this offers maximum flexibility for smaller operations, it becomes increasingly difficult to manage as your organization grows and can create security gaps if not properly maintained.
Mandatory Access Control (MAC) involves system-controlled access based on security clearance levels, typically used by government contractors or businesses handling highly sensitive information. This model requires careful implementation but provides the highest security level for businesses with strict compliance requirements.
Access control systems deliver immediate improvements to your security posture while streamlining daily operations. You gain the ability to protect sensitive areas like server rooms, executive offices, research facilities, or inventory storage areas with precision. Rather than worrying about lost keys or unauthorized copying, you can control access based on roles, schedules, or temporary needs.
Real-time visibility into facility usage patterns helps optimize operations and identify potential security concerns before they become problems. You can see which employees are in the building, track high-traffic areas, and monitor after-hours access attempts. This information proves invaluable for everything from energy management to emergency evacuation procedures.
The ability to instantly revoke access when employees leave or contractors complete projects eliminates the security window that exists with traditional key systems. No more wondering if former employees returned their keys or whether contractors made copies during their project tenure.
Modern systems also support compliance requirements across various industries by maintaining detailed audit trails. These logs provide concrete evidence for investigations, help meet regulatory requirements, and can reduce liability exposure by demonstrating your commitment to security best practices.
Today’s access control systems work best when integrated with your existing security infrastructure. Video surveillance integration allows you to automatically capture footage when someone accesses restricted areas or when access is denied. This combination provides both verification and evidence collection capabilities.
HR system integration streamlines employee onboarding and termination processes by automatically updating access permissions based on employment status changes. When new employees join your Pittsburgh business, their access credentials can be automatically configured based on their role and department.
Visitor management integration creates seamless experiences for clients and temporary workers while maintaining security protocols. Visitors can receive temporary credentials through email or text messages, eliminating the need for physical badges while ensuring access expires automatically.
Building automation integration allows access control systems to trigger lighting, HVAC, and other building systems based on occupancy patterns. This integration can significantly reduce energy costs while ensuring comfortable working environments for your team.
Start your access control planning by conducting a thorough security assessment of your facility. Identify which areas require restricted access, who needs access to various zones, and what your compliance requirements include. Consider both current needs and future growth plans, as retrofitting access control systems can be more expensive than implementing scalable solutions from the beginning.
Scalability becomes crucial even if you’re starting with just a few controlled doors. Specify systems that can expand as your business grows, whether that means adding more access points, accommodating additional users, or integrating with other security technologies. Cloud-based platforms typically offer the most scalability while reducing ongoing IT maintenance requirements.
Budget considerations should include both upfront costs and long-term operational expenses. While cloud-based systems may have higher monthly fees, they often reduce total cost of ownership by eliminating server hardware, reducing IT support needs, and providing automatic software updates.
Consider the user experience for your employees and visitors. Systems that are difficult to use or slow to respond can create productivity bottlenecks and user frustration. Look for solutions that balance security requirements with operational efficiency.
Mobile credentials are increasingly popular among Pittsburgh businesses because they eliminate the need for physical cards or fobs. Employees use their smartphones to access doors, reducing credential management overhead while providing enhanced security through device authentication.
Biometric authentication offers the highest security level by using unique physical characteristics like fingerprints or facial recognition. While more expensive to implement, biometric systems eliminate the possibility of lost, stolen, or shared credentials.
Time-based access control allows you to automatically restrict access based on schedules, holidays, or special events. Employees can access the building during business hours while contractors might only have access during specific project timeframes.
Anti-tailgating technology prevents unauthorized individuals from following authorized users through access points. This feature becomes particularly important for businesses with high-security requirements or valuable assets.
Implementing access control systems requires expertise in security technology, local building codes, and integration requirements. The complexity of modern systems means that proper installation and configuration are crucial for both security effectiveness and operational reliability.
TN Security Pittsburgh specializes in commercial access control systems throughout the greater Pittsburgh area. Our team understands the unique security challenges facing local businesses and can design solutions that meet your specific requirements while staying within budget constraints. We handle everything from initial security assessments through system installation, user training, and ongoing support.
Whether you’re securing a small office building or a large commercial facility, we provide comprehensive access control solutions that integrate seamlessly with your existing security infrastructure. Our experience with Pittsburgh’s diverse business landscape: from healthcare facilities to manufacturing plants: ensures your system is designed for your industry’s specific needs.
Ready to enhance your business security with modern access control technology? Contact TN Security Pittsburgh at 412-967-0467 or visit our offices at 3287 Library Road, Pittsburgh, PA 15234. You can also reach our team directly at sales@teamnutztechnology.com to schedule your security consultation and learn how access control systems can protect your business while improving operational efficiency.